It's a Free Lunch. 100% unpatented,
open-source freeware:
Why?
FiveLoaves is an Internet utility designed to meet the most common
needs of internet users - primarily secure connectivity. The simple case
of User-to-User over the internet as well as the more complex
Employee-to-Employer, and even the most complex - namely Business-to-Business.
Networking is Networking. A home computer and an office
computer require the same software solution to achieve connectivity. The
main difference arises in the placement of firewalls, and routing across
multiple internal corporate networks - issues that often arise when connecting
Employee-to-Employer, and nearly always arise when connecting
Business-to-Business.
FiveLoaves primary purpose is secure connectivity. In the
cases of Employee-to-Employer and Business-to-Business, this often means a
Windows-to-Unix, or Unix-to-Windows, or often in the case of
Business-to-Business... Windows-to-Unix-to-Windows. With
this functionality implemented as the foundation of the application - Five
of the most basic needs of internet users have been implemented into an open
source architecture that can be easily extended to provide additional future
services - An example of a software
abstraction framework.
- The ability to transfer files from one machine to
another, like FTP - but securely - (did you know FTP is not secure?). FTP just tosses everything on the same machine (a server) and
cannot reach any internal machine (a peer), therefore FTP is Client-Server, this
utility is Peer-to-Peer. Either end can initiate the connection so firewalls can
be safely bypassed.
- A Web Server
(like Apache or IIS)
it runs my site http://www.unitedbusinesstechnologies.com/
My site uses: static HTML, static images, static java script and an outsourced
SSL web store. There is no bridge to COM or Java from this web server.
Speed, Simplicity, and Security are the primary design objectives - what
many people really NEED in a web server. See step 7 of the setup
instructions for details.
- The ability to control mouse and keyboard from
remote (like PCAnywhere). but with the framework supplied connection
routing, encryption, and compression enabled. This service is based on a
public software project called VNC, managed by AT&T. I modified
their protocol handshake, and
statically linked their DLL's into this single 356kb(on Win32) executable.
Although VNC does work in Linux and Unix I did not get them linked into version
1.0, they're coming - with multi-port display support.
- Tunneling TCP data (like SSH or
http://www.http-tunnel.com/), but the
tunnel can bounce across ANY number of points, AND gives the user full control over the
entire connection route network and hardware.
- Circuit level TCP
Proxy (like
Proxy Server or Delegate),
but with load balancing, fail-over , and firewall
elusive technology. Plus better performance and much higher connection
limits than delegate.
Posted July 2, 2002 - "Microsoft responds! On my machine with
"auto-upgrade" turned on, this
popped up. The other half of the patch only works for their
firewall. The real challenge is this: Microsoft - Can you stop
anyone from invoking IE through COM and intercepting the 'passing' HTTP headers,
modify the request then take over the response? It's a simple dynamic
proxy, is that your suggestion for a version 2 feature?. Your lock was taken, and your chain link fence can't stop anybody
either. (My Souvenirs)
Your next product will be this: Encrypted and Proprietary
communication between browser and firewall . Your GUI is nice and COM is cool,
but it's so slippery that Nimda modified the guest user's privileges on my NT
server. That's pretty slippery. Tagging
is a popular sport these days. You're it. Enjoy your 4th of
July weekend while you celebrate freedom. Don't forget where it came from."
Some of this
software will no longer work with a proprietary firewall.
Complete Setup
Instructions can be found here
5Loaves is a network of tunnels. The simplest connection-route is
between two points. The first point is the user's own machine. This is the
"tunnel entry point". From there - a connection may bounce
directly to the destination or to a machine that can reach the
destination or to a machine that can be reached by the
destination..
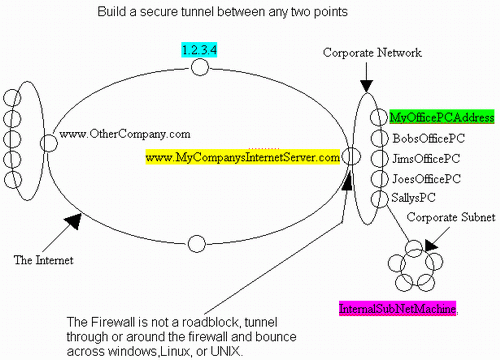
For example if you used the
Remote Workstation Controller or File Transfer applications to connect to a
machine called www.MyCompanysInternetServer.com
- then the information travels between the application and the tunnel entry
point in the clear (the entry point is on the same machine as the application).
Once the data is ready to leave your workstation it is encrypted and sent to the
first and only destination - a machine called www.MyCompanysInternetServer.com.
On that machine the data is decrypted and forwarded to correct application.
Consider this connection-route: www.MyCompanysInternetServer.com|MyOfficePCAddress
This time the data enters the tunnel on your machine (at home or elsewhere) and
is encrypted with the password only know by a machine called MyOfficePCAddress.
The data travels to the first machine called www.MyCompanysInternetServer.com. www.MyCompanysInternetServer.com
couldn't
see the data if it wanted to because it's encrypted with a key that it does not
know. There is a small delivery header that it can read. That header instructs www.MyCompanysInternetServer.com
to proxy this connection to another machine called MyOfficePCAddress.
Since that machine is the last in the connection-route, the data is
decrypted and forwarded to the correct port on that machine.
This type of connection-route has no depth limits. For example here is a 3 point
connection route:
www.MyCompanysInternetServer.com|MyOfficePCAddress|InternalSubNetMachine
This is just like the first example but it causes the connection to be bounced
to a machine even deeper in the network called InternalSubNetMachine.
Each machine in the connection route must be running 5Loaves.
This all assumes your network admin is a wise and reasonable person who truly
understands that properly used encryption is safe. Some network administrators
won't want people to have that kind of remote access - so they will refuse to
install 5Loaves on www.MyCompanysInternetServer.com.
Department managers are often wiser than the network administrators. They can
outsource an internet server for as little as 200/month - or use their own
broadband machine at home to run 5Loaves with the SwitchBoardServer option
enabled. Suppose that machine has no public DNS so rather than a name it just
has an IP address like 1.2.3.4.
SEE YOUR IP ADDRESS
Now if you can't go through the firewall - just go around it. (actually through
it from the other side)
You set MyOfficePCAddress to poll
for a connection named MYOfficePCConnectionName on 1.2.3.4
Now you can use a connection route like this from home:
1.2.3.4|~MYOfficePCConnectionName
This causes the client application (Remote Workstation Controller or File
Transfer or other) to enter a tunnel on your own machine - encrypt with
the data with the password for MyOfficePCAddress,
but send the data to 1.2.3.4. Now the connection will sit there until some
machine comes to pickup a connection named MYOfficePCConnectionName. Then
the connection will be bounced to that machine - which must know the secret key
in order to decrypt the data.
If you have a very secure office network, you might have some machines that are
not on the internet. You can access those machines too. Suppose MyOfficePCAddress
can reach a machine called InternalSubNetMachine,
but that machine cannot route to the internet. Run 5Loaves on both machines and
from home connect like this:
1.2.3.4|~MYOfficePCConnectionName|InternalSubNetMachine
This goes around the firewall
to your office PC then bounces down into the secure corporate subnet - securely.
If you are the network admin - the office users will be grateful for the remote
access.
If you're not the network admin - don't tell your network admin - he'll never
know you're doing it.
If you're a developer, a tunneling system like this can really come in
handy. If you ever need to move a file securely from one place to another
from your own application.... just run 5Loaves on both machines - generate the
file, then send a command to 5Loaves that causes it to deliver the file (encrypted
an compressed over the wire). The source code has examples of this
for both Java and C++, it's a very simple process that can be achieved in
almost any programming language in just a few lines of code.
If you're a C++ developer that needs to build a custom 'web service', 5Loaves
is a 'service framework' that you could add your own services to with unmatched
performance. Mission critical applications, might even choose
this framework over something like .NET that provides no portability, and many
often unwanted features that become future security and administration
liabilities. If you need COM and support for many other COM based
technologies, then this is not the tool you want.
If you are a UNIX user, you may enjoy "remote root" telnet sessions that
tunnel in as localhost connections.
Extra Credit Points
-
100% pure ANSI C++
- very portable
-
It compiles into a 472kb Binary in Solaris using Forte 7
-
It compiles into a 427kb Binary in Red Hat Linux 7.1 using
gcc
-
5Loaves is only 356kb
(Win32 uncompressed)
- well suited for embedded/handheld systems.
-
It runs as a service in
Windows. (type 5LoavesSvc.exe -install) or (5LoavesSvc.exe -remove)
-
It loads NO (non-kernel) SO's or DLL's.
(reduce failure points + more secure + easy
upgrades)
Disclaimer
-
This is "just out of the oven"
(as of April 30, 2002) and keep in mind it's only version 1.0
-
I'm gathering the TODO list
for version 2 - Feel free to contribute:
-
5Loaves@UnitedBusinessTechnologies.com
-
It was heavily
tested on 98 & 2K. I verified all functionality in Linux. I only
compiled it on Solaris.
Credits
 General
General  News
News  Suggestion
Suggestion  Question
Question  Bug
Bug  Answer
Answer  Joke
Joke  Praise
Praise  Rant
Rant  Admin
Admin 






