Introduction
Code security is the main aspect in .NET development. Helping protect Web sites against unauthorized access is a complex issue for Web developers. ASP.NET provides web application protection with the help of the .NET framework and IIS (Internet Information Services). In this article, we take a short tour of Authentication and Authorization concepts. I think it will be helpful for beginners.
Background
I would like to thank Abhijit Jana for his nice article on IIS 6.0 for beginners. His article encouraged me to write some text on Authorization and Authentication. This article will give you basic idea about authentication and authorization and its working in WebApplication.
What is Authentication
Basically authentication and authorization are two interrelated things. First authentication is done and then authorization. Authentication means checking Is valid User? In depth authentication is the process of getting identification credential such as name and password from a user and validating those credentials against some authority. If the credentials are valid, it means once an identity has been authenticated, the authorization process starts.
.NET uses the following authentication providers for authentication:
- Windows Authentication
- Forms Authentication
- .NET Passport Authentication
Before getting deeper in the authentication, let us have a look at authorization.
What is Authorization
Authorization is the process of determining what rights the authenticated user has?
By using authorization, we can limit access rights by granting or denying specific permissions to an authenticated identity. The purpose of authorization is to determine whether an identity should be granted the requested type of access to a given resource.
There are two fundamental ways to authorize access to a given resource:
- URL authorization
- File authorization
Let's start with the authentication providers.
Windows Authentication
This is the default authentication provider of .NET. ASP.NET uses windows authentication with the help of IIS.
Authentication is performed by IIS in the following ways:
- Integrated Authentication
- Basic Authentication
- Digest Authentication
- Anonymous Authentication
When IIS authentication is complete, ASP.NET uses the authenticated identity to authorize access. IIS can be configured so that only Windows domain users can log in.
Integrated Authentication
This authentication is also known as Windows NT Challenge/Response authentication. Integrated Windows authentication is enabled by default for Windows Server 2003 operating systems. The application here uses challenge/response protocols or kerberose to authenticate users.
Although Integrated Windows authentication is secure, it does have two limitations:
- Only Microsoft Internet Explorer versions 2.0 and later support this authentication method.
- It does not work over HTTP proxy connections.
Integrated Windows authentication is best suited for an intranet environment.
Basic Authentication
This Authentication needs a user name and password to connect over network, but the given password is sent in plain text. Hence it is a non secure authentication.
The following steps show how basic authentication works:
- The Web browser displays a dialog box for a user to enter user name and password.
- Then, it attempts to establish a connection with server using user's credential.
- If the user credentials are rejected, the browser displays authentication dialog box to validate again.
- If the user credentials are accepted, then it establishes connection with server.
It has some advantages and disadvantages as follows:
- Advantage: It is part of the HTTP specification and is supported by most browsers.
- Disadvantage: Browsers transmit user password in plain text format over the network.
Digest Authentication
In this type of authentication, password is hashed before it is sent across the network. Digest Authentication transmits credential across the network as an MD5 HASH or message digest However, to be using Digest Authentication, we must use Internet Explorer 5.0 or above. The username and IIS running IIS must be of the same domain.
Anonymous Authentication
It is very open and public authentication. When user attempts to open a site, IIS will not check for any authentication.
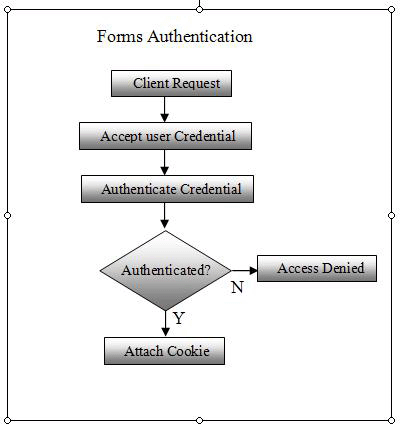
Forms Authentication
The user provides credentials and submits the form. If the user authenticates successfully, the system issues a cookie that contains a credential or key for getting identity.
Forms authentication is a good choice if your application needs to collect its own user credential at logon time through HTML forms. In this authentication, we can customize content for known user. Basically in this case, the system accepts credential from user (mostly username and password). The application code checks the credential to confirm authenticity. If the credentials are authenticated, application code attaches a cookie containing username not password. If the credentials fail, then request return with access denied message.
Let the following picture clear the idea:
.NET Passport Authentication
Microsoft .NET Passport is a user-authentication service and a component of the Microsoft .NET framework. Passport authentication is a centralized authentication service and .NET Passport uses standard Web technologies and techniques, such as Secure Sockets Layer (SSL), HTTP redirects, cookies, Microsoft JScript, and strong symmetric key. Sign in sign out and registration pages are centrally hosted rather than being specific to an individual site.
There is no real time or server to server communication between participating Web sites and the central .NET Passport servers.
To enable an authentication provider for an ASP.NET application, create an entry in Web.config file as follows:
//Web.config file
<authentication mode="[Windows|Forms|Passport|None]" />
The default authentication mode is Windows. If we set the authentication mode as None, then ASP.NET will not apply any authenticate checks on client request.
None authentication can be useful when you want to introduce custom authentication scheme or don't want to check any authentication for getting highest level of performance.
URL Authorization
URL authorization maps users and roles to pieces of the URL namespace. By using this authentication, we can selectively allow or deny access to certain sets, users, or roles. You just need to place a list of users and roles in the <allow> or <deny> elements of <authorization> section.
There are two special identities that we can allow or deny:
| * | Refers to all identities |
| ? | Refers to anonymous identity |
Consider the following example which will emphasis the subject:
<authorization>
<allow users="ABC"/>
<allow roles="XXX"/>
<deny users="XYZ"/>
<deny users="?"/>
</authorization>
The above example grants access to ABC user and users of XXX roles. Whereas it denies access to XYZ user and anonymous users.
We can give multiple users in a single element:
<authorization>
<allow users="ABC, XYZ"/>
</authorization>
If you want to deny access to all users, then the setting is as follows:
<authorization>
<deny users="*"/>
</authorization>
File Authorization
File authorization is active when you use Windows authentication. It will check the access of file. For that, it does an access control list (ACL) check of the .aspx or .asmx handler file to check if user has a access of that file. Applications can further use impersonation technique to check the resources that they are accessing. The file access is checked against the NTFS file permission. The checking ensures that the user has the READ access of the requested file. The default user account is ASPNET account.
Impersonation is the technique in which the logged in user acts like an authenticated entity. By default, the Impersonation is not enabled. We can set the impersonation in web.config file:
<identity impersonate="true"/>
or we can provide a username and password to the impersonation. Username suggests on which behalf user is working on a site.
<identity impersonate="true" userName="administrator" password="pass"/>
We can enable these settings from IIS also.
Finally, that is all about the basic idea of authentication and authorization.
Summary
Let us take a snap tour of what we learnt. To improve the security of web applications, ASP.NET and IIS introduce Authentication and Authorization processes.
- Authentication is a process of checking if a use is valid
- Authorization is a process of checking what access the authenticated user has
- You can use [Windows/Forms/Anonymous/.NET passport/None] authentication
- You can use [File/URL] authorization
If you have your application run on intranet, then you should use Windows authentication. This will keep track of all users on the intranet. Otherwise, Forms authentication could be a good choice.
References
Knowledge is an endless entity. We have to learn more and get more. I used the following references to write this article:
History
- 30th January, 2010: Initial post
 General
General  News
News  Suggestion
Suggestion  Question
Question  Bug
Bug  Answer
Answer  Joke
Joke  Praise
Praise  Rant
Rant  Admin
Admin