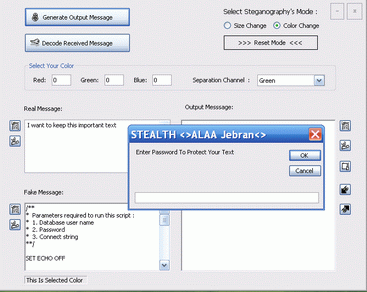
Introduction
Our goal is to build a simple application that is able to send and receive encrypted messages embedded in Rich Text Format: *.DOC, *.RTF, EMAIL /MessageBody/, etc. The user has the ability to choose the fake text he wants and the program must be able to tell whether or not this fake text will suit the real text.
The user can set a different password for every message he sends. This will enable the manager to transmit to two groups two different messages with two different passwords using the same fake text. Thus, you will be able to send encrypted and hidden messages in any source code that you choose! Just take a look at the EXE to see for yourself.
How does it work?
We will not change the text itself, but we will change the unseen attributes of the text. These attributes are many and it is impossible for web servers to track them all. There are lots of Steganographic methods and tracking them will waste huge amounts of processing for uncertain results. Be aware that Steganography is more effective than encryption when used in the right way. The deletion of all attributes is not an option, so we will choose the size and the color. This figure will underscore my point:
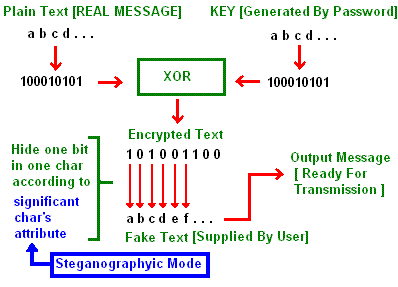
Size change mode
In this mode, we will change the size of the characters in the fake text according to the selected font size and differential factor. We will use 2 sizes, X1 and X2. X1 is the selected font size and X2 is the selected font size plus the differential factor. Bit 0 is represented by the occurrence of the character whose size is X1. Bit 1 is represented by the occurrence of the character whose size is X2.
Behold! Not all fonts support any size you choose, so the program will recommend that you decrypt your message before you send it to make sure that the font supports your {X2} size. The recipient must have the same font that you use installed in his machine. This will probably not be a problem to you because there is a wide range of font families in common between Windows OS versions. The recipient must also know the selected font size that you use for decryption. After we hide the real message in the fake message, the rest of the fake message characters will be sized as X1.
Color change mode
This is the more recommended mode for use, as it is very stable and safe. In this mode, we will change the color of the chars in the fake text according to the selected color and the program's calculated color. We will use 2 colors, X1 and X2. X1 is the selected color and X2 is the program's calculated color. The program will search to find the nearest color for which it is impossible to recognize the difference with naked eye. Bit 0 is represented by the occurrence of the character whose color is X1. Bit 1 is represented by the occurrence of the character whose color is X2. The recipient must know which color you have chosen for decryption. After we hide the real message in the fake message, the rest of the fake message characters will be colored as X1.
When do we stop?
We shall not use certain characters from the plain text alphabet. That is to say, when we will get a particular character we will stop output message generation. In this way we prohibit users from using that character, so don't underestimate any input character. Here is an example.
Example
Imagine using "/ " as the 'End Of Message' sign, but some user may like to send a messages like this:
/ \ \ / \ \ \ / \ / \ \ \ \ \ / \ /
"Now," you ask, "what is this?" This is another encrypted message where {/,\} stand for bits {0,1}. So, this is an encrypted bits stream. If you decrypt it, you will have bits. Then if you convert them to bytes, they can be anything: image, text, word document, sound, etc. Here, we decrypted some encrypted steganographic text -- in the visible fake message -- to have steganographic encrypted text, i.e. invisible / \ / \ / /... This was a doubled steganography. We could add a new layer of steganography if the output bytes were a Word or RTF file. For a big Word or RTF file, these things are more than possible because storage size is divided by 8. This is not so bad, as a normal text book with 800 pages can have the required size.
As you have probably noticed, we need to store extra information for size. We will use 4 bytes to store the size. This means 4 * 8 bits or 32 bits, i.e. the first 32 characters in the fake text. We will take every 2 digits in size number and store them in 1 byte. Here you can see that the first 32 characters in the fake text are extremely important, even if they are unseen characters such as spaces.
How to use it?
There are Paste and Clear buttons for every text box, besides the Import and Export buttons for the Output text box. First of all, copy any big useless text and use the Paste button near the fake text box to paste it. Write your real message in the real message text box. The program will tell you about the required capacity of the fake text. Don't use huge fake text for small real messages, as this will increase the processing time.
Try to cut text from the fake message to have optimum capacity, i.e. the smallest capacity that is bigger than the required capacity. This is shown above the real message text box. Next, select your mode and supply the password you want. If you used size mode, verify that font size differences in the output message are invisible. Otherwise, change the font size and try again untill you see that the differences are invisible. You can use the spaces trick, too, as it is mentioned later. Then export the output message to the RTF File using the Export button. That's it! Now you can attach it to your email and send it anywhere.
Using the code
I have outlined the main procedures that will unhide text in text. The code is commented for every step.
subs encrypter1 encrypter2 handles hiding according to mode 1 2
subs decrypter1 decrypter2 handles unhiding according to mode 1 2
Size mode
size mode :
Public Sub decrypter1(ByRef errflag As Boolean)
errflag = False
TextBox1.Text = ""
Dim tm As String = RichTextBox1.Text
Dim cont As Double = -1
Dim rt As New RichTextBox
Dim ba As bits_array
ba.Initialize()
Dim sz As Long
Dim sz1, sz2, sz3, sz4 As Byte
Dim m As Long
For m = 0 To 7
cont = cont + 1
RichTextBox1.Select(cont, 1)
If RichTextBox1.SelectionFont.Size = Me.user_size Then
ba.bits(m) = False
Else ba.bits(m) = True
End If
Next m
bits_to_byte(sz1, ba)
For m = 0 To 7
cont = cont + 1
RichTextBox1.Select(cont, 1)
If RichTextBox1.SelectionFont.Size = Me.user_size Then
ba.bits(m) = False Else ba.bits(m) = True
End If Next m
bits_to_byte(sz2, ba)
ba.Initialize()
For m = 0 To 7
cont = cont + 1
RichTextBox1.Select(cont, 1)
If RichTextBox1.SelectionFont.Size = Me.user_size Then
ba.bits(m) = False
Else ba.bits(m) = True
End If
Next m
bits_to_byte(sz3, ba)
ba.Initialize()
For m = 0 To 7
cont = cont + 1
RichTextBox1.Select(cont, 1)
If RichTextBox1.SelectionFont.Size = Me.user_size Then
ba.bits(m) = False
Else
ba.bits(m) = True
End If
Next m
bits_to_byte(sz4, ba)
ba.Initialize()
sz = sz1 + 100 * sz2 + 10000 * sz3 + sz4 * 1000000
If sz = 0 Or sz >= ( 99 99 99 99 ) Then
MsgBox("Error: Font Doesn,t Support This Size")
errflag = True
Exit Sub
End If
MsgBox("The Used Differential Factor Is : " +
Me.Differential_f.ToString, MsgBoxStyle.Information)
Dim i As Long
Dim output As String = ""
For i = 1 To sz
ba.Initialize()
For m = 0 To 7
cont = cont + 1
RichTextBox1.Select(cont, 1)
If RichTextBox1.SelectionFont.Size = Me.user_size Then
ba.bits(m) = False
Else
ba.bits(m) = True
End If
Next m
//
bits_to_byte(sz1, ba)
output = output + Chr(sz1).ToString
Next i
Dim passw As String = ""
input("Enter Password To Decrypt Your Text", passw)
If passw = "" Then
MsgBox("User Canceled.")
errflag = True
Exit Sub
ElseIf passw.Length < 4 Then
MsgBox("Error ! Password Is Too Short.")
errflag = True
Exit Sub
End If
process_pass_with_tx(passw, output)
Dim je As Long
je = output.Length - 1
output = output.Substring(0, je)
TextBox1.Text = output
Color mode
color mode :
RichTextBox1.Select(current_char, 1)
If RichTextBox1.SelectionColor =
ColorTranslator.FromWin32(Me.user_rgb_big) Then
ba.bits(m) = True
Else
ba.bits(m) = False
End If
Points of interest
- You can't use *.txt files to paste an output message because it doesn't support RTF.
- When you paste the output message in a Word document, the recipient needs to open the attached Word file. He must use Select all and aste it using the Paste button in the Output message section of the application.
- Similar steps must be followed when you paste the output message in the body of the email message.
- If you use an RTF file to carry your output message Export button, then you must use the Import button to obtain the delivered output message. This is the most recommended way for transmission and reception because when you use the RTF file of the output message as an email attachment, you guarantee that the output message formation will not suffer any distortion. Also, the output message will be delivered completely to the recipient. This will not engender suspicion. For example, someone might send lectures or source code files to someone as email attachments and it would not be out of the ordinary.
- When you paste the output message in the body of the email message, note that if your email composer doesn't support the font then the program may show unexpected behavior. The recipient in this case will probably have an error message when he tries to start decryption. This is why I again recommend exporting the message to an RTF file so that you can attach it to your email.
- When you have the agreement of someone to transmit using this program, then you two must agree on the parameters of the transmission. He must know the color degree you use or the font size you use, otherwise he will not be able to decrypt what you send. Of course, you have to give him the password too.
- The capacity of fake text -- i.e. the amount of letters that can be embedded in the fake text -- will be automatically displayed in GUI when you try to write a new letter in the fake text box.
- The capacity of real message -- i.e. the amount of letters in the fake text box needed to carry your real message -- will be automatically displayed in GUI when you try to write a new letter in the real text box. These online flags are designed to save you time, as you will not get an error of <Fake text is not big enough> when you start the encryption process.
- If you find that the required differential factor has caused visible differences when you use the Size mode, then you can solve the problem in this way: Fill the beginning of the fake text box with spaces. These spaces will carry the encrypted message and because they are unseen characters, your differential factor will cause no damage to the rest of the seen characters, i.e. the fake text. The recipient can decrypt your message using the same font size but with another differential factor. Why? Because bits generation in the decryption process depends on the size of the used font only.
- The Textbox control has a maximum amount of characters it can hold. If your text is bigger than that, try to separate it and use a new fake text for each part.
- I did something weird in the code in that I added one space at the beginning of every fake text and I did the same to the beginning of the real message. This space will tell us if someone has played with the text during transmission.
- Of course, you can change the encryption algorithm to any one you trust.
- As a user, remember to choose strong keys (passwords) for your messages.
History
- 19 June, 2007 -- Original version posted
 General
General  News
News  Suggestion
Suggestion  Question
Question  Bug
Bug  Answer
Answer  Joke
Joke  Praise
Praise  Rant
Rant  Admin
Admin 







 ).
).