This article is a continuation of a couple of articles about identity management for an MVC application. We covered embedding identity management within the application and then added role-based authorization. Below are the links to the articles:
Embedded Application Identity Part 1: Basic Identity Management in ASP.NET MVC 5: http://www.codeproject.com/Articles/770341/Embedded-Application-Identity-Part-Basic-Identit
Embedded Application Identity Part 2: Role-Based Authorization in ASP.NET MVC 5: http://www.codeproject.com/Articles/770345/Embedded-Application-Identity-Part-Role-Based
The next step in improving the security of our enterprise applications would be to decouple the user and role management from the application.
Windows authentication is the form of authentication in ASP.NET that uses an Active Directory domain controller to authenticate the user. Active Directory is Microsoft's flagship Identity management product. There are several advantages for using Windows authentication over forms authentication for enterprise application from our prior articles:
- User credentials are not passed over the network wire (if the user has joined the domain)
- Identity management can be managed by a department separate from development
- The same user account can be used by other enterprise applications and services without the need for replicating the accounts to other apps.
Like forms authentication, when a user is authenticated using Windows authentication, a token is created that is passed along as a browser cookie to subsequent ASP.NET requests indicating that the user has previously been authenticated.
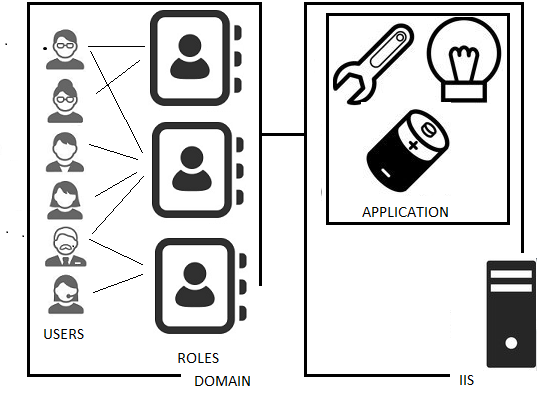
Below is an image that summarizes the architecture of the system. Now the application is just one piece of the architecture. We have externalized the users and roles to Active Directory called and the application also hosted on IIS. The application will use it's host system - IIS - to join the domain and verify the credentials supplied by the user with the domain controller before allowing the web request to be completed.
In this article we will demonstrate how to setup our Footloose Financial Services enterprise application for Windows authentication. This will involve the following steps:
- Modify the application code and configuration for Windows authentication
- Setup a Windows Server 2012 Active Directory domain controller
- Setup a Windows Server 2012 IIS web server
- Deploy the Visual Studio project to the web server
Get the application ready for Windows authentication
There are some code and configuration changes in Visual Studio that we will need to make to the application to support Windows authentication. Fortunately it is mostly removing code and code files. I will go over them briefly but the revisions can be viewed in the github project at
https://github.com/pcarrasco23/FootlooseFinancialServices under the revision labeled "Modifications for Windows authentication and IIS".
Identity management is delegated to the Active Directory domain controller
Most of the functionality in AccountController.cs has been removed. The identity management functionality provided by Active Directory makes most of the code in this file unnecessary. With Active Directory, user accounts are created and passwords are managed by an internal IT department separate from development.
I also removed the bootstrap code in Startup.Auth.cs that configured the forms authentication cookie properties. The forms authentication cookie will be replaced by a token from IIS after a user is authenticated to use the application. The configuration of this token is performed by an administrator in the IIS Manager.
Enable the WindowsPrincipal provider in ASP.NET
If you remember from the previous article, the
IPrincipal interface is used by ASP.NET developers to get information about the user that has been authenticated to use the application. For ASP.NET applications to use Windows authentication, the
WindowsPrincipal implementation of IPrincipal must be injected into the ASP.NET worker process. WindowsPrincipal implements the IPrincipal interface which basically means that is has code that can get the user's Windows group membership. To configure ASP.NET to use WindowsPrincipal the authentication mode must be changed to "Windows" in the application web.config.
<system.web>
<authentication mode="Windows" />
</system.web>
Setup a Windows Server 2012 Active Directory domain controller
The next step is setting up the Active Directory domain controller if you do not have one setup already. If you work for a company and are using this example within your company's enterprise network then this step has most likely already been done (assuming the company you work for uses a Windows domain). If you are using this example from home then I will show you how to setup a virtual Windows Active Directory using free or trial versions of VMWare Player and Windows 2012 Server. You will need plenty of memory on your computer to run this effectively (I have 8GB on my computer).
Install VMWare Player and Windows Server 2012
VMWare Player allows you to run a virtual operating system for free on your home computer (not for commercial use). In this article we will be running Windows Server 2012 on VMWare Player . You can download VMWare Player here: https://my.vmware.com/web/vmware/free#desktop_end_user_computing/vmware_player/6_0
The current version of VMWare Player as of this writing is 6.0.2. You can download an evaluation copy of Windows Server 2012 here (again not for commercial use): http://technet.microsoft.com/en-us/evalcenter/hh670538.aspx
When you download Windows Server 2012 you will want to have the ISO file available because you will start up your new VMWare virtual using the ISO.
Open VMWare Player and select "Create a New Virtual Machine" and make sure that the "I will install the operating system later" option is checked in the dialog box that opens.

Select "Microsoft Windows" as the guest operating system and select "Windows Server 2012" as the version. Then enter a name for the virtual machine (I called it "AD Domain Controller") and choose a location for the virtual machine. The virtual should be allocated at least 60 GB. at this point you can customize the virtual hardware. I recommend at least 2GB of memory for the virtual machine for optimal performance.
Once the virtual machine has been created, go back to the main VMWare screen, select the newly created virtual, and click "Play virtual machine". The virtual system will bootup. Cancel the boot with the ESC key and then press CTRL-ALT to take control of the boot process. Click the "Change CD\DVD Settings" to select the ISO.

Select the Windows Server 2012 Eval ISO that you previously downloaded and then click the "Restart VM" button. Now the virtual machine will start with the ISO and the Windows Server 2012 installation will start.
Installing and Configure Active Directory on Windows Server 2012
Once the Windows Server 2012 installation is complete we will then install the Active Directory domain controller role.
There are many good examples of setting an AD domain controller on the Internet including this one by Rackspace that I followed very closely: http://www.rackspace.com/knowledge_center/article/installing-active-directory-on-windows-server-2012
I won't cover this step-by-step but I will illustrate the configurations for my particular installation. For my example I create a new forest (as opposed to adding a domain controller to an existing forest) and domain controller. The domain name that I used for my AD domain controller installation was footloosefs.com.
When you are finished with the domain controller setup, you will be ready to create service accounts, groups, and users in your AD domain. Under Tools, open Active Directory Users and Computers.

Create Service Accounts
At this point we will go ahead and create a domain service account and group for the IIS web server (which we will create and configure next). The reason why we need to create a domain service account is that the web server that hosts the enterprise application will most likely need to communicate with other domain services in the network (such as other web services or SQL Server or Exchange Server for email functionality) and it will need to authenticate with a domain account in order to do this. Also it's good practice to assign the service account to a domain group so that we can apply access control policies to multiple service accounts at the same time at the group level.
The names that I used are my personal choice and you can use any names that you want but be sure to remember what they are when you are configuring the IIS web site. A service account is a domain user of which the password does not expire. When you create these users make sure that you select the "Password never expires" option.
First create a group called "Web Service Accounts". The group scope should be "Global" and the group type should be "Security". Then create a service account to act as the identity for the application pool of the web server (I called it FootlooseFSWebUser) and make it member of the Web Service Accounts group.

Create Application Roles and Users
Now we need to create roles and users for the application. These users and roles correspond to the users and roles that we created in the previous articles but now we are creating them in Active Directory instead of in the ASP.NET Identity database.
First lets create the roles. Right-click on Users and select New -> Group. Create a new group called "Admin". This will correspond to the Admin roles created in the previous article about role-based authorization. Then create the Demographics, Financial, and Online Access groups.
Now let's create the users. Right-click on User and select New -> User. Create a user called "Advisor Web Admin" and make it a member of the Admin group. Then create another user called "Richard Delany" with the login "rdelany" and make him a member of the Demographics group.
Lastly take note of the IP address of the AD domain controller. We will need it when configuring the IIS server and connecting it to the domain.
Installing and Configure IIS 8.0 on Windows Server 2012
The next step will be to install IIS 8.0 on a Windows Server 2012 machine or virtual. Our Footloose Financial Service web application will be hosted on IIS and we will need to install IIS and specific features of IIS for ASP.NET development and Windows authentication.
1. Configure the server to communicate with the AD domain.
2. Install IIS.
2. Create and the configure the web site and application pool.
3. Deploy the Visual Studio project redistributable files to the web site.
Configure the server to communicate with the AD domain
Once Windows Server 2012 has been installed on the virtual we need to configure it to communicate with the Active Directory domain controller.
Windows hosts in a Active Directory domain use the DNS (Domain Name Server) protocol to communicate with the domain controller. First we need to configure the TCP/IP DNS settings of the server so that when sends DNS queries to the AD domain controller. Open the Control Panel, go to Network and Sharing Center. Select the Ethernet interface and click the Properties button. Then select "Internet Protocol Version 4" and click the Properties button. Click the option "Use the following DNS server addresses" and enter the IP address of the AD domain controller. This will work in our example but typically in production this is done by a proxy web server which is outside the scope of this article.

Now that the server has the ability to resolve the domain name footloosefs.com, we can join the server to the domain. Go back to the Server Manager and click the domain link. This will bring up the System Properties dialog. Click the Change button, select the Domain option, and enter the name of the domain (footloosefs.com).

At this point we will need to restart the virtual machine.
Install IIS
If you are using the 2 server architecture then you will want to spin up another instance of a Windows Server 2012 VMWare virtual and install the Web Server (IIS) role on that virtual. If you are using the 1 server architecture then you can install the Web Server role on the same machine as the AD domain controller. If your computer has sufficient resources for both virtuals I would recommend spinning up another virtual machine for IIS because this architecture mirrors most corporate networks. This article from Rackspace demonstrates how to install IIS 8.0 on a Windows Server 2012 instance: http://www.rackspace.com/knowledge_center/article/installing-iis-80-on-windows-server-2012
When you are installing the IIS role be sure to select the "Windows Authentication" option in the security section of the Web Service options. This feature is not installed by default when installing IIS and our web application will need this feature of IIS to implement it's identity management.

Don't click Next yet! We also need to install the ASP.NET 4.5 and Server Side includes features of IIS under the "Application Development" section in order for our application to function properly. When you select ASP.NET 4.5 you will be prompted to install other components required by ASP.NET 4.5 . Click the "Add Features" button to continue.

Create and the configure the web site and application pool
Now that IIS has been installed we need to create and configure the web site and application pool. First we need to determine the physical location on the server of the web site files (web site DLLs, web pages, JavaScript files, CSS files, etc). For simplicity I chose the C drive and named the folder the name of the web site: C:\advisor.footloosefs.com\advisor. At this point the folder will be empty but go ahead and create the physical folders because you will need this in place when creating the web site.
From the Tools menu open Internet Information Services Manager.
Create and configure the application pool. Create a new Application Pool called "advisor.footloosefs.com" with the .NET Framework version of v4.0 and the managed pipeline mode should be Integrated. Under Advanced Settings of the application pool, the Identity should be FOOTLOOSEFS\FootlooseFSWebUser or the domain account that you created in the previous section to be the identity of the web site.
Create the web site and physical directory structure. Create a new web site called "advisor.footloosefs.com". Add a virtual directory called "advisor". Under Advanced Settings of the virtual the physical directory should be C:\advisor.footloosefs.com\advisor or the physical path of the web site that you created beforehand. The Application Pool of the virtual should be advisor.footloosefs.com or the name of the application pool that you created. All requests to this web site and virtual will in the process of the advisor.footloosefs.com application pool.
Bind to http services to port 80 and configure the host header. Select the web site advisor.footloosefs.com and click the Bindings link. Click the Add button and the default should be port 80. Change the Host Name field to advisor.footloosefs.com and click OK. This will cause IIS to forward any http request with the host header of advisor.footloosefs.com and port 80 to this web site.

Enable Window Authentication and disable all other authentication schemes. Again select the advisor.footloosefs.com web site and open the Authentication feature in the IIS section. Disable all other authentication except for Windows Authentication which should be enabled. This will make all requests to this web site to send back a http 401 challenge that will validate the username and password credentials against the footloosefs.com domain (since that is the domain that the IIS server has joined).
Configure the web site physical directory
Copy the Visual Studio project redistributables to the web site physical directory. This is where you will need to get a little creative. There are a number of way you can copy the output of the Visual Studio project to the web site physical directory. I just used a thumb drive to copy the files over. Another option is the Web Deploy tool. It is a component you install on the IIS server that will allow you to deploy the redistributable files from the Visual Studio project to the IIS directory.
http://www.iis.net/downloads/microsoft/web-deploy
The structure of the physical directory should look like below.

Configure NTFS permissions. Finally we have to give domain authenticated users access to the physical directory of the web site. Right-click on the advisor.footloosefs.com directory and click Properties and then click the Security tab. Add Authenticated Users of the footloosefs.com domain to the directory NTFS ACL with Read & execute, List folder contents, and Read permissions.

Add a DNS A record for the web site
We want internal hosts to access the web site using the URL http://advisor.footloosefs.com/advisor instead of having to type the IP address of the web server. First get the IP address of the web server using the "ipconfig" command. Also Server Manager > All Server will give you the IP address of the server.
Now let's go back to the AD domain controller and add a DNS entry for the web site URL advisor.footloosefs.com. More specifically we are going to add a DNS A record which maps a logical domain name to an IP address. From the Tools menu, select "DNS" to open the DNS Manager. Click "Forward Lookup Zones" and right-click on the footloosefs.com zone and select New Host (A or AAAA). Enter "advisor" in the Name field. The Fully qualified domain name will automatically be populated. Then enter the IP address of the web server.

After you save the A record open a Powershell command window enter execute the commands "ipconfig /flushdns" and "ipconfig /registerdns" to clear and update the DNS tables. Now advisor.footloosefs.com will resolve to the web server's IP address for any internal host that is using the AD domain controller as the primary DNS server.
Test the web application from an internal host
Now we are ready to verify that the application is accessible from another host in the network. Remember that any host that is accessing the web site must have the IP address of the AD domain controller as the primary DNS server in order for advisor.footloosefs.com to resolve to the IP address of the web server.
Open a web browser and enter the URL http://advisor.footloosefs.com/advisor. You will be prompted to enter valid credentials of a user in the footloosefs AD domain. First enter the credentials of the Admin user advisorwebadmin. Then search of account holders and select an account holder. Note that all 3 of the tabs are available because the web site code will confirm that the user is in the Admin role which resolves to the Admin AD group when the web site is using Windows Authentication.
Logoff and then login as Richard Delany (rdelany). Search for account holders and select an account holder. Note that there is only one tab because the authenticated user is in the Demographics role, the users of which only are authorized to view the Person tab. The Demographics role resolves to the Demographics AD group.
Conclusion
We covered quite a bit in this article but moving a enterprise application from your local developer machine to a corporate production enterprise network involves many steps including setting up an AD domain controller and an IIS server. Using the IPrincipal .NET interface for managing identities in our application allowed us to move from ASP.NET Identity to Active Directory user store with minimal code changes. The Active Directory domain controller decouples identity management from the application so that the identities in the AD domain can be used to authenticate other enterprise applications and services. DNS is the TCP/IP application level protocol that Active Directory hosts use to communicate with the AD domain controller. The application redistributables must be moved to a physical directory on the IIS server so that they can be configured to be accessible to AD domain users.
In the next article we will discuss how these Active Directory identities can be use to authenticate applications and services in the cloud.
