Introduction
Interesting characteristic (for me!) of the .NET Framework is the possibility to simulate situations that were possible using the language assembler x86. I refer, in particular, to the STACK (sequence of data). The Stack can be considered (reductively) as an area of "temporary memory" in which the data is visible in inverse order to that of the insertion.
Background
To emulate another programming language in order "to confuse" the code against the decompilers!
Using the code
In .NET, therefore, class STACK is present. The main methods exposed from the .NET class STACK are following:
PUSH
Inserts the value in the stack. Equal instruction is present in the assembler language x86.
POP
Extracts the value from the stack. Equal instruction is present in the assembler language x86.
PEEK
Law a value from the stack.
COUNT
Counts the elements on the stack.
Example:
Dim st As New Stack
st.Push(1)
st.Push(2)
st.Push(3)
Debug.WriteLine(st.Count)
Debug.WriteLine(st.Peek)
st.Pop()
Debug.WriteLine(st.Count)
Debug.WriteLine(st.Peek)
st.Pop()
st.Pop()
Debug.WriteLine(st.Count)
Understanding how the stack works in insertion/extraction of the data (*always* in inverse order), we are ready to implement our algorithm of cryptography. We want to realize it (relatively simple), effective, it turns out to you always random and that it comes dynamically executed from the compiler... then we want to construct a creative... Poly-Engine Crypter for the strings (...ehila! Who has said like the poly-engines present in the virus code? *yes* is the answer!). In this tutorial, I introduce to you *only* implementing dynamic code using the functions of: sum, subtraction, XOR (for the nostalgic programmers of the assembler language x86: add, sub, XOR) of byte.
We imagine of wanting to hide (crypt) the string:
Hello Word! (hex value: 48 65 6C 6C 6F 20 57 6F 72 64 21)
Dim _myStr As String = "Hello Word!"
Dim rand As New Random
Dim _count As Integer
Dim _valCrypt As Integer = 0
Dim _value As Integer
Dim ik As Integer
Debug.WriteLine("Dim st As New Stack(" & CStr(_myStr.Length - 1) & ")")
Debug.WriteLine("Dim bCrypt As Integer = 0")
For ik = _myStr.Length To 1 Step -1
_count = rand.Next(0, 3)
_value = Asc(Mid(_myStr, ik, 1))
Debug.WriteLine(PolyEngineWrite(_valCrypt, _count, _value))
Debug.WriteLine("st.Push(bCrypt)")
Next ik
Private Function PolyEngineWrite(ByRef valCrypt As Integer, _
ByVal count As Integer, _
ByVal value As Integer) As String
Dim tempVal As Integer
Select Case count
Case 0
tempVal = (valCrypt - value)
Case 1, 3
tempVal = (valCrypt Xor value)
Case 2
tempVal = (value - valCrypt)
End Select
tempVal = tempVal And 255
valCrypt = value
Return ("bCrypt = StackDecrypt(bCrypt, " & CStr(count) & ", &H" & Hex(tempVal) & ")")
End Function
Two output examples:
| Output Example 1: |
Output Example 2: |
Dim st As New Stack(10)
Dim bCrypt As Integer = 0
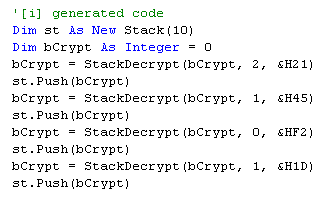
bCrypt = StackDecrypt(bCrypt, 2, &H21)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 1, &H45)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 0, &HF2)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 1, &H1D)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 2, &HE8)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 2, &HC9)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 0, &HB1)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 0, &H3)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 0, &H0)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 0, &H7)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 2, &HE3)
st.Push(bCrypt)
|
Dim st As New Stack(10)
Dim bCrypt As Integer = 0
bCrypt = StackDecrypt(bCrypt, 0, &HDF)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 1, &H45)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 1, &H16)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 0, &H3)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 0, &H18)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 0, &H37)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 1, &H4F)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 2, &HFD)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 2, &H0)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 2, &HF9)
st.Push(bCrypt)
bCrypt = StackDecrypt(bCrypt, 1, &H2D)
st.Push(bCrypt)
|
01. 00h + 21h = 21h (!)
02. 21h xor 45h = 64h (d)
03. 64h - F2h = 72h (r)
04. 72h xor 1Dh = 6Fh (o)
05. 6Fh + E8h = 57h (W)
06. 57h + C9h = 20h (space)
07. 20h - B1h = 6Fh (o)
08. 6Fh - 03h = 6Ch (l)
09. 6Ch - 00h = 6Ch (l)
10. 6Ch - 07h = 65h (e)
11. 65h + E3h = 48h (H) |
01. 00h - DFh = 21h (!)
02. 21h xor 45h = 64h (d)
03. 64h xor 16h = 72h (r)
04. 72h - 03h = 6Fh (o)
05. 6Fh - 18h = 57h (W)
06. 57h - 37h = 20h (space)
07. 20h xor 4Fh = 6Fh (o)
08. 6Fh + FDh = 6Ch (l)
09. 6Ch + 00h = 6Ch (l)
10. 6Ch + F9h = 65h (e)
11. 65h xor 2Dh = 48h (H) |
...the code result is always different!
The bytes comes manipulated from the StackDecrypt procedure and inserted into the stack with PUSH method (see introduction):
Private Function StackDecrypt(ByVal bCrypt As Integer, _
ByVal iOpCode As Integer, _
ByVal iSalt As Integer) As Integer
Select Case iOpCode
Case 0
bCrypt = (bCrypt - iSalt)
Case 1, 3
bCrypt = bCrypt Xor iSalt
Case 2
bCrypt = (bCrypt + iSalt)
End Select
bCrypt = bCrypt And 255
Return bCrypt
End Function
**Now it does not remain that "to recompose" the string from the stack. For this last passage, we can use (continuation of the two examples of output):
Dim str As String = ""
Dim ij As Integer
For ij = 1 To st.Count
str &= Chr(st.Pop)
Next ij
...the final string obtained from the dynamic process of the code decryption is: Hello Word!
Points of Interest
In a future article, I will explain as it is possible to generate dynamic code in assembler language x86 and recalling it with one execution callback!
With these techniques, I try to implement secure code against the decompiler. It must be used in combination with an obfuscator and a crypter. It will be available soon, my .NET crypter ;-).
For other information, please visit my web site (in continuous modernization).
History
July 2004: First public release (sorry for my bad English...I'm Italian.)
