Introduction
In the process of writing programs, I need to read the BcdOSLoaderBoolean_KernelDebuggerEnabled value. I searched the web for a long time, but could not find
any source code or methods. I also found that some people were looking for answers. So I wrote this function. I hope this function is helpful to everyone. If you are interested
in this article, I know why. You know that BcdOSLoaderBoolean_KernelDebuggerEnabled is the member of BcdOSLoaderElementTypes.
typedef enum BcdOSLoaderElementTypes {
BcdOSLoaderDevice_OSDevice = 0x21000001,
BcdOSLoaderString_SystemRoot = 0x22000002,
BcdOSLoaderObject_AssociatedResumeObject = 0x23000003,
BcdOSLoaderBoolean_DetectKernelAndHal = 0x26000010,
BcdOSLoaderString_KernelPath = 0x22000011,
BcdOSLoaderString_HalPath = 0x22000012,
BcdOSLoaderString_DbgTransportPath = 0x22000013,
BcdOSLoaderInteger_NxPolicy = 0x25000020,
BcdOSLoaderInteger_PAEPolicy = 0x25000021,
BcdOSLoaderBoolean_WinPEMode = 0x26000022,
BcdOSLoaderBoolean_DisableCrashAutoReboot = 0x26000024,
BcdOSLoaderBoolean_UseLastGoodSettings = 0x26000025,
BcdOSLoaderBoolean_AllowPrereleaseSignatures = 0x26000027,
BcdOSLoaderBoolean_NoLowMemory = 0x26000030,
BcdOSLoaderInteger_RemoveMemory = 0x25000031,
BcdOSLoaderInteger_IncreaseUserVa = 0x25000032,
BcdOSLoaderBoolean_UseVgaDriver = 0x26000040,
BcdOSLoaderBoolean_DisableBootDisplay = 0x26000041,
BcdOSLoaderBoolean_DisableVesaBios = 0x26000042,
BcdOSLoaderInteger_ClusterModeAddressing = 0x25000050,
BcdOSLoaderBoolean_UsePhysicalDestination = 0x26000051,
BcdOSLoaderInteger_RestrictApicCluster = 0x25000052,
BcdOSLoaderBoolean_UseBootProcessorOnly = 0x26000060,
BcdOSLoaderInteger_NumberOfProcessors = 0x25000061,
BcdOSLoaderBoolean_ForceMaximumProcessors = 0x26000062,
BcdOSLoaderBoolean_ProcessorConfigurationFlags = 0x25000063,
BcdOSLoaderInteger_UseFirmwarePciSettings = 0x26000070,
BcdOSLoaderInteger_MsiPolicy = 0x26000071,
BcdOSLoaderInteger_SafeBoot = 0x25000080,
BcdOSLoaderBoolean_SafeBootAlternateShell = 0x26000081,
BcdOSLoaderBoolean_BootLogInitialization = 0x26000090,
BcdOSLoaderBoolean_VerboseObjectLoadMode = 0x26000091,
BcdOSLoaderBoolean_KernelDebuggerEnabled = 0x260000a0,
BcdOSLoaderBoolean_DebuggerHalBreakpoint = 0x260000a1,
BcdOSLoaderBoolean_EmsEnabled = 0x260000b0,
BcdOSLoaderInteger_DriverLoadFailurePolicy = 0x250000c1,
BcdOSLoaderInteger_BootStatusPolicy = 0x250000E0
} BcdOSLoaderElementTypes;
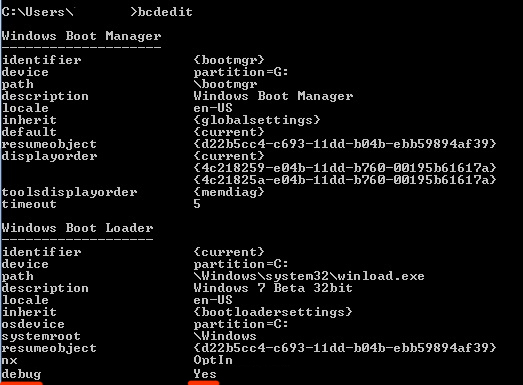

Using the code
bool detect_KernelDebugger_status()
{
DWORD type;
DWORD size=500;
BYTE Data[500];
HKEY hKey;
char sysDir[MAX_PATH];
GetSystemDirectory(sysDir,MAX_PATH);
LONG retsult=RegOpenKeyEx(HKEY_LOCAL_MACHINE,
"SYSTEM\\MountedDevices\\",
0,
KEY_READ,
&hKey);
if(retsult!=ERROR_SUCCESS)
{
find_Flag=0;
}
sysDir[2]=0;
char sysdriver[50];
sprintf(sysdriver,"\\DosDevices\\%s",sysDir);
retsult=RegQueryValueEx( hKey,
sysdriver,
NULL,
&type,
&Data[0],
&size);
memcpy(&Driver_type,Data,sizeof(int));
RegCloseKey(hKey);
bool KernelDebuggerEnabled;
find_Flag=0;
RegSearch (HKEY_LOCAL_MACHINE,"BCD00000000\\Objects\\","");
if(find_Flag)
{
KernelDebuggerEnabled=(bool)Kernel_Debug_Enabled;
}
else
{
KernelDebuggerEnabled=false;
}
return KernelDebuggerEnabled;
}
Note: Use a recursive function to enumerate.
#define MAX_KEY_LENGTH 255
TCHAR pathElement[MAX_KEY_LENGTH];
bool find_Flag;
DWORD Kernel_Debug_Enabled;
DWORD type;
DWORD size = sizeof (Kernel_Debug_Enabled);
int Driver_type;
int Driver_type_21000001;
void RegSearch(HKEY hKey, TCHAR rootKey[], TCHAR path[])
{
DWORD numSubKey=0;
DWORD i;
DWORD sizeSubKey;
TCHAR subKey[MAX_KEY_LENGTH];
TCHAR pathnow[MAX_KEY_LENGTH];
LONG retsult=RegOpenKeyEx( hKey,
rootKey,
0,
KEY_READ,
&hKey);
if(retsult!=ERROR_SUCCESS)
{
find_Flag=0;
strcpy(pathElement,path);
return;
}
if (RegQueryValueEx( hKey,
"Element",
NULL,
NULL,
NULL,
NULL)==ERROR_SUCCESS)
{
if(strstr(path,"260000a0")||strstr(path,"260000A0"))
{
BYTE data_21000001_Element[300];
DWORD OS_LOADER_TYPE;
DWORD _type;
DWORD _size=sizeof(DWORD);
char temp[300];
char sub_Description_path[300];
char sub_21000001_path[300];
sprintf(sub_Description_path,"BCD00000000\\Objects\\%s",path);
char* p=strstr(sub_Description_path,"}\\");
*(p+2)=0;
strcpy(temp,sub_Description_path);
sprintf(sub_Description_path,"%s%s",sub_Description_path,"Description\\");
sprintf(sub_21000001_path,"%s%s",temp,"Elements\\21000001\\");
HKEY _hKey=HKEY_LOCAL_MACHINE;
LONG retsult=RegOpenKeyEx( _hKey,
sub_Description_path,
0,
KEY_READ,
&_hKey);
retsult=RegQueryValueEx(_hKey,
"Type",
NULL,
&_type,
(BYTE*)&OS_LOADER_TYPE,
&_size);
RegCloseKey(_hKey);
_hKey=HKEY_LOCAL_MACHINE;
retsult=RegOpenKeyEx( _hKey,
sub_21000001_path,
0,
KEY_READ,
&_hKey);
_size=300;
retsult=RegQueryValueEx(_hKey,
"Element",
NULL,
&_type,
data_21000001_Element,
&_size);
RegCloseKey(_hKey);
memcpy(& Driver_type_21000001,&data_21000001_Element[56],sizeof(int));
if((Driver_type_21000001==Driver_type)&&(OS_LOADER_TYPE==0x10200003))
{
find_Flag=1;
RegQueryValueEx( hKey,
"Element",
NULL,
&type,
(BYTE *) &Kernel_Debug_Enabled,
&size);
sprintf(pathElement,"HKEY_LOCAL_MACHINE\\BCD00000000\\"
"Objects\\%sElement=%x",path,Kernel_Debug_Enabled);
return;
}
else
{
goto next;
}
}
else
{
goto next;
}
}
else
{
next: RegQueryInfoKey( hKey,
NULL,
NULL,
NULL,
&numSubKey,
NULL,
NULL,
NULL,
NULL,
NULL,
NULL,
NULL);
if (numSubKey)
{
for (i=0; i<numSubKey; i++)
{
subKey[0]='\0';
sizeSubKey=MAX_KEY_LENGTH;
RegEnumKeyEx( hKey,
i,
subKey,
&sizeSubKey,
NULL,
NULL,
NULL,
NULL);
sprintf(pathnow,"%s%s\\",path,subKey);
RegSearch (hKey,subKey,pathnow);
}
}
}
RegCloseKey(hKey);
}
If someone has a better solution, can you share it?
 General
General  News
News  Suggestion
Suggestion  Question
Question  Bug
Bug  Answer
Answer  Joke
Joke  Praise
Praise  Rant
Rant  Admin
Admin 









 Please try again.
Please try again.