Disclaimer
NeCoders shall not be held responsible for any cases of software/files being hacked due to the information provided in this article.
General Overview
I always believe Security is the number 1 priority in building a good software. I have been trying to make sure that security issues are considered during my design stage. But the problems with current students in tertiary education is that I can say most of them never actually consider security as a real issue. They tend to focus more on the system's features and GUI. Lecturers also hardly pay attention or encourage students to place higher security measures into their projects, which I think is something not appropriate at all.
Why should we be aware of security?
1st Scenario :
In my current smart card company, most of the information stored within our SDK are highly confidential. We do not want our SDK to be manipulated by our competitors.
2nd Scenario :
You took a year to write a software and in the process consumed a lot of resources and time for its development. Then you sell your software, you find that all your hard work in past 12 months were easily manipulated. Therefore, steps must be taken to ensure this does not happen.
3rd Scenario :
One day, my manager came to me and asked me this question.
Questions: Are .NET assemblies that secure?
Answer: Nothing is secure, but all we can do is to try to make things harder for a hacker.
Then he gave me this reply; I thought .NET is supposed to be more secure. That is why we move into Microsoft .NET. He was total upset when I showed him the .NET Reflector program by Lutz Roeder which you can decompile your binaries back to C# source code. Below is an example of how it looks like.
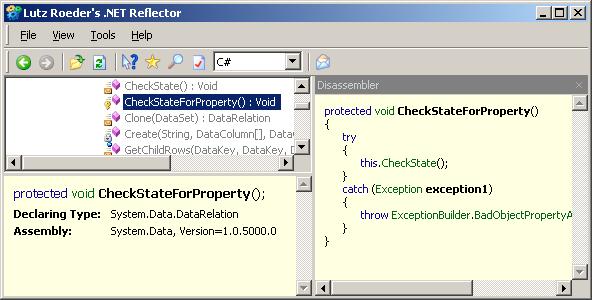
The Demonstration
4th Scenario :
Back in 1990s, you may have noticed that some shareware programs implements this kind of verification technique. When you install the software, it will create a key in the Windows registry. Basically what it does, is stores the serial number inside the registry as either a plain text or encrypted version. Yes, I have seen people placing plain text in registry. So when your program runs, it will check the registry to verify the existence that particular key. If you have a wrong serial number or that particular key is not there, it will prompt you an error. Right now I will try to simulate this verification technique in C# step by step.
Test machine specifications
Steps to do
1. Go to Windows XP's start menu and select 'Run...'. Type
"regedit" or
"regedt32".

2. Navigate to \HKEY_LOCAL_MACHINE\Software, then right click and choose New > Key
3. Name the Key to NeCoders. When you are done, right click the NeCoders key, and choose New > String value. Name it to serial.

4. Double-click on the serial string and enter "1111-1111-1111-1111" as the value.

5. Okay, now launch your Visual Studio .NET 2003.

6. Create a new C# window application project and name it CrackingIL.

7. The C# window application designer will be loaded as below.

8. Now follow the specifications as below.
| Controls | Name | Text | Fonts |
| Form | FrmSecureApp | Secure App 1.0 | Arial, Size 10, Bold |
| label | lblheader | Welcome to NeCoders | - |
9. You should have something like this:

10. Now double-click on the FrmSecureApp form. The FrmSecureApp load event will be generated.

11. Now add this code into the event:

12. Once done, build the project by pressing F5.

13. Nothing unusual. It is just a windowed form so what is so special about it?
14. When the program runs, it will check the registry for these conditions:
Check the existence of HKEY_LOCAL_MACHINE\SOFTWARE\Necoders
Check the existence of HKEY_LOCAL_MACHINE\SOFTWARE\Necoders\serial
Checks whether the serial string value equivalent with “1111-1111-1111-1111”
15. Now open up your registry edit, and change the string value of serial to “1111-1111-1111-1112”. Now press F5 again in Visual Studio .NET 2003 to debug the software.

It fulfills (iii).
16. Next, try to delete the serial string value from NeCoders key. Press F5 again.

It fulfills (ii).
17. Finally, delete the NeCoders key. Press F5.

It fulfills (i).
18. Now I am thinking hard how to break this licensing technique. This is the fun part and hope you will like it. Right now, no matter how you run your C# windows form, it will prompt you the same error “Please acquire a license to run this!”. Please bear this in mind.
Note: There is no difference in breaking a Debug or Release mode assemblies.
19. Go to Windows Start > Programs > Microsoft Visual Studio .NET 2003 > Visual Studio .NET Tools > Visual Studio .NET 2003 Command Prompt.
20. Change to the directory where your CrackingIL.exe is resided.
21. Type ildasm CrackingIL.exe /out=CrackingIL.il

22. If you notice, there will be 3 files added to your debug folder.

23. Open CrackingIL.il with any text editor. I used notepad.
24. You will see some assembly codes. This is in intermediate language. Cool huh?

25. Scroll down until you get this.

The highlighted is actually your FrmSecureApp_Load event which you created earlier on in Visual Studio .NET 2003. 26.
Okay, now what we want to do is to remove the portion of code that calls the registry checking. Just remove all the codes from IL_0000 to IL_0075. You will end up with this.

27. Reopen your Visual Studio .NET 2003 command prompt and type 'ilasm CrackingIL.il'.

28. Once done, try to run CrackingIL.exe.

You should see this. If you do, congratulations for you have successfully cracked CrackingIL.exe.
Conclusion
I hope you like this article even though it is a simple one. See Part 2 for the next one in this series. If you still have any doubts, just email me.
References
 General
General  News
News  Suggestion
Suggestion  Question
Question  Bug
Bug  Answer
Answer  Joke
Joke  Praise
Praise  Rant
Rant  Admin
Admin 








