Introduction<o:p>
After a long search for a simple and secure file encryption utility, that is simple and intuitive to use I've decided to write something of my own.<o:p>
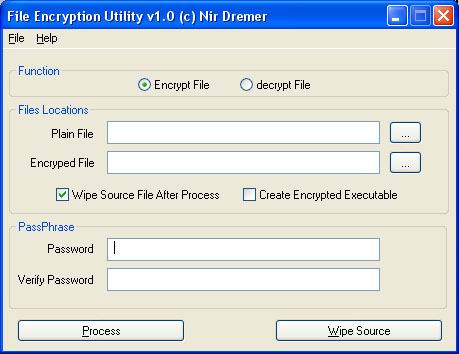
File Encryption utility is a simple tool for encrypting both text and binary files using the blowfish encryption algorithm.<o:p>
The utility can create a self extracting encrypted file. For a deep view of how to create a self extracted executable check my other article: Creating Self-Extracted Executable .<o:p>
Features<o:p>
File Encryption Utility Has the following features:<o:p>
-
Fast & Quick File Encryption/Decryption.<o:p>
-
Internal File Wiping Utility.<o:p>
-
Creating Self-Extracting Encrypted File.<o:p>
-
Explorer Integration (through Configuration Dialog).<o:p>
-
Command Line Parameters.<o:p>
Language<o:p>
The File Encryption utility is writen in native C++ using ATL only for windowing classing.<o:p>
The usage of ATL is minimal so anyone who is not familiar with the library should be able to understand the code as well.<o:p>
Overview<o:p>
File Encryption Utility is divided to few small projects:<o:p>
-
FileEnc – The UI of the file encryption utility, also containing the Processing class which is also used by SelfExtract and it is responsible for reading/writing files.<o:p>
-
Enc_Blowfish – Blowfish encryption implementation (based upon Bruce Schneier and Jim Conger implementation).<o:p>
-
SelfExtract – Self Extracting executable "header".<o:p>
-
GenLib – Small Library holding all commonly used items in other project parts.<o:p>
-
Builder – Small Console utility for creating the final File Encryption Executable.<o:p>
GenLib – The General Library<o:p>
In order to save time and to have a central point for all general purpose classes I'm working with a static library called GenLib.<o:p>
A stripped version of the GenLib is available with the File Encryption Utility. In this version you can see the following general purpose classes:<o:p>
-
GenFiles – Openning OpenFile/SaveFile and OpenDirectory Dialog Boxes.<o:p>
-
SelfExtract – Creating Self-Extracting Executable.<o:p>
-
Thread – Implementation of a parent class for classes who want to execute code in separate thread (more information can be seen in the header – thread.h).<o:p>
-
FileWipe – Wiping a File from Hard Drive.<o:p>
All those classes are under the GenLib namespace.<o:p>
Additional Encryptions<o:p>
Inside the FileEnc project there's an interface called EncryptionInterface – implementing this interface can allow you to easily change the encryption the utility uses.<o:p>
Implementing this interface requires only stream cipher implementation and saves all the overhead of working with files.<o:p>
Blowfish implementation is statically linked to the utility in order to avoid hacking by changing the dll. With a few minutes of work the utility can support a number of encryption dlls that can be loaded at runtime based on the users decision.<o:p>
Security<o:p>
In order to make the utility the most secure I can I've tried wiping information from memory when the application closes.<o:p>
When looking at the source, you can see that I've used ZeroMemory API and few others APIs to delete information from memory (like the password used).<o:p>
When encrypting a file you can mark the 'Wipe Source After Process' checkbox and by that insure that the file you're encrypting is not accessible.<o:p>
Remarks<o:p>
Decryption does NOT verify password correctness (information is being encrypted without adding any information about the file). As a result when decrypting with the wrong password you will receive a file with junk inside - this is not a bug.<o:p>
The file encryption is based upon the password length - larger passwords equal better security.<o:p>
Although I believe that the file wiping method is very secure, to be 100% sure you should use a product dedicated to that purpose.<o:p>
Reference<o:p>
Blowfish encryption algorithm - http://www.schneier.com/paper-blowfish-fse.html
Revision History
23 Sep 2002 - Initial Revision
Nir is a Product Manager from Israel with past Software Engineering Experience.
You're welcome to visit his photography site:
http://www.dremer.net/
 General
General  News
News  Suggestion
Suggestion  Question
Question  Bug
Bug  Answer
Answer  Joke
Joke  Praise
Praise  Rant
Rant  Admin
Admin 








![Rose | [Rose]](https://codeproject.global.ssl.fastly.net/script/Forums/Images/rose.gif)
![Beer | [beer]](https://codeproject.global.ssl.fastly.net/script/Forums/Images/beer.gif)

