Introduction
The fractal encryption algorithm uses the famous Mandelbrot fractal to convert the encryption key (provided by the user) to a longer key that is subsequently XORed with the plain text (provided by the user) resulting in an encrypted text. The algorithm as explained and implemented herein below is new, invented by me in a moment of creativity (i.e. after lunch, around 14.30, with eyes half closed), and coded during the next morning: this means that it could by chance be a very strong encryption algorithm, BUT it could also be the opposite (i.e. an encrAption algorithm), and thus it comes with no warranty.
Many famous encryption algorithms expand (to a certain degree) the given encryption key and then, after moving, shifting and replacing the bits in the clear text, they XOR it with the expanded password, and this process is usually repeated a certain number of times. The fractal algorithm tries to create a more 'random' expanded key using the mandelbrot fractal, instead of using a fixed rule.
Furthermore, the fractal algorithm encrypts the whole file as a single big block, instead of encrypting it split in 256 bits blocks (so it does not use the same encryption key on every block, but uses only one big encryption key to encrypt the whole clear text (which should mean: less repetition --> less chance of successful attack).
Background
To understand this algorithm, it could help to have a mild background on fractals, complex math and knowing what the gauss plan is; and, of course knowing also something about cryptography doesn't hurt.
To understand the small downloadable 'notepad-like' project I made to test this algorithm, it could be interesting to have a look to the Scramble Anagram algorithm, since in this project I used it together with the fractal algorithm and the simple XOR.
Using the code
The core of the algorithm is contained in the downloadable zip file, in the file MyCryExtensions.cs, in the function 'Cry_FractalCoding', inside the block of code delimited by "#region calculate expanded key".
The encryption consists in the repetition of some binary operations inside a loop, among which there is the calculation of the fractal encryption key.
Before executing the fractal algorithm, the encryption key provided by the user is expanded: since the algorithm is applied many times (defined by the variable 'countloops'), and since every loop needs a 10 bytes long key, the expanded key will be 10 * countloops bytes long. The expansion of the key is performed by the function Cry_ExpandKey, and it is quite simple.
Now....
First: a region on the Gauss plan is defined. This region is delimited by a rectangle with variable width and height, placed around the upper half of the black circumference indicated in the following picture.
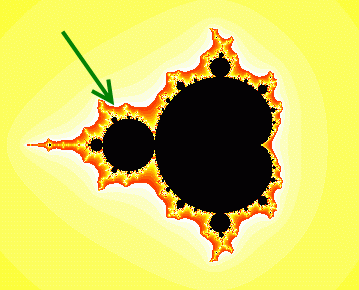
The exact boundaries of that rectangle are:
double gX1 = -1 - ((double)BitConverter.ToUInt32(expandedkey, 0 + ky) / (double)uint.MaxValue) / 4;
double gY1 = 0 + ((double)BitConverter.ToUInt32(expandedkey, 4 + ky) / (double)uint.MaxValue) / 10;
double gX2 = gX1 + 0.25;
double gY2 = 0.25 + gY1;
Complex bottomleft = new Complex(gX1, gY1);
Complex topright = new Complex(gX2, gY2);
where
expandedkey is the previously mentioned expanded key, and ky is the position of the starting byte for every encryption loop.
Second: the defined region is used to create an array of Complex numbers, called gaussarray.
int squaresize = Convert.ToInt32(Math.Sqrt(len)) + 1;
Complex[] gaussarray = GetGaussArray(squaresize + expandedkey[8 + ky], squaresize + expandedkey[9 + ky], bottomleft, topright);
where len is the length of the byte array containing the user clear data.
The GetGaussArray function merely partitions the gauss rectangle (found in the first part) as a big squared rectangle, where the cohordinates of every square are subsequently put in gaussarray.
Third: every point (complex number) inside the
gaussarray is iterated by calling the function
IterateMandelbrot (same operation done by the fractal drawing programs). The Mandelbrot function is:
Z(n+1) = Z(n)^2 + c;
c is the complex number to be iterated,
Z(0) is the initial function value and is set to ZERO; so
Z(1) = c; then
Z(2) will be calculated from
Z(1) etc. If at any point of the calculation, the real or the imaginary part of
Z(n) diverge (i.e.
double.IsInfinity(Z.Real) or
double.IsInfinity(Z.Imaginary) then the value of
n is returned; if, on the other hand,
Z is not diverging after 256 calculations, then it will return ZERO...
All the returned values are reduced by modulo 256 (to fit in a byte) and put in a byte array called countiterations.
Fourth: the countiterations array has now to be purified (since they say that too many repetitions could weaken an encryption): No zeroes are allowed in this array, and no more than three identical consecutive values are allowed. After the purification, the countiterations array will be the sought fractal encryption key.
Fifth: use the fractal encryption key with one or more encryption algorithms. In the provided example (the one in the downloadable zip file), three operations are made on the clear data, using this key: ScrambleBitLeft, Xor, ScrambleByteRight. While xor is pretty obvious, the explanation of the other two can be found in the the article referenced in the 'Background' section.
Sixth: the points from the First to the Fifth are repeated 7 times. (Why seven? Because many repetitions give a more secure encryption, but they also slow down the process; so seven times on my PC was a good compromise, since this seems to be a very slow algorithm).
And that's all, folks.
 General
General  News
News  Suggestion
Suggestion  Question
Question  Bug
Bug  Answer
Answer  Joke
Joke  Praise
Praise  Rant
Rant  Admin
Admin 










 long (and it increases in lenght depending on the lenght of the clear text): the longer is the key, the more secure is the encryption; and in this case, there isn't key repetition within the whole message.
long (and it increases in lenght depending on the lenght of the clear text): the longer is the key, the more secure is the encryption; and in this case, there isn't key repetition within the whole message. moment), I would like to: 1- produce a fractal key which is always bigger than the clear text: 2- create a new key expansion algorithm based on the fractals (to replace the simpler key expansion function provided with the current article).
moment), I would like to: 1- produce a fractal key which is always bigger than the clear text: 2- create a new key expansion algorithm based on the fractals (to replace the simpler key expansion function provided with the current article). I forgot to attach to the project... , but I did it now, so you'll see it when this new version will be approved; sorry: this is my first attachment in an article) I did't merely xor, but I scrambled the result at each encrypting loop, so to make the result more secure than by applying a simple xor.
I forgot to attach to the project... , but I did it now, so you'll see it when this new version will be approved; sorry: this is my first attachment in an article) I did't merely xor, but I scrambled the result at each encrypting loop, so to make the result more secure than by applying a simple xor.