Get Information About the Currently Logged-on Users - Part 2
3.55/5 (9 votes)
Apr 18, 2006
4 min read
97486
1954
Get information about the currently logged-on users - in remote computer
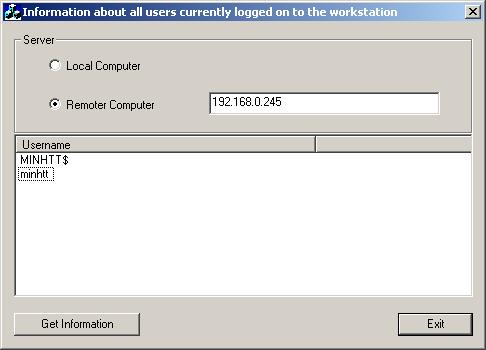
Introduction
When you work in a network and you manage more users, you need to know information about the currently logged-on user, on the local computer and on the remote computer. In part 1, we get information for currently logged-on user on the local computer. In this article, we get information of all logged-on users on the remote computer
We use function NetWkstaUserEnum:
NET_API_STATUS NetWkstaUserEnum(
LPWSTR servername,
DWORD level,
LPBYTE *bufptr,
DWORD prefmaxlen,
LPDWORD entriesread,
LPDWORD totalentries,
LPDWORD resumehandle
);
Security Requirements
Windows NT
Only members of the Administrators local group can successfully execute the NetWkstaUserEnum function both locally and on a remote server.
Windows 2000
If you call this function on a domain controller that is running Active Directory, access is allowed or denied based on the access-control list (ACL) for the securable object. The default ACL permits all authenticated users and members of the "Pre-Windows 2000 compatible access" group to view the information. By default, the "Pre-Windows 2000 compatible access" group includes Everyone as a member. This enables anonymous access to the information if the system allows anonymous access.
If you call this function on a member server or workstation, all authenticated users can view the information. Anonymous access is also permitted if the RestrictAnonymous policy setting allows anonymous access.
Windows XP
If you call this function on a domain controller that is running Active Directory, access is allowed or denied based on the ACL for the securable object. To enable anonymous access, the user Anonymous must be a member of the "Pre-Windows 2000 compatible access" group. This is because anonymous tokens do not include the Everyone group SID by default.
If you call this function on a member server or workstation, all authenticated users can view the information. Anonymous access is also permitted if the RestrictAnonymous policy setting permits anonymous access. If the RestrictAnonymous policy setting does not permit anonymous access, only an administrator can successfully execute the function.
Parameters
- servername
- [in] Pointer to a Unicode string specifying the name of the remote server on which the function is to execute. The string must begin with \\. If this parameter is
NULL, the local computer is used.
- [in] Pointer to a Unicode string specifying the name of the remote server on which the function is to execute. The string must begin with \\. If this parameter is
- level
- [in] Specifies the information level of the data. This parameter can be one of the following values.
Value Meaning 0 Return the names of users currently logged on to the workstation. The bufptrparameter points to an array ofWKSTA_USER_INFO_0structures.1 Return the names of the current users and the domains accessed by the workstation. The bufptrparameter points to an array ofWKSTA_USER_INFO_1structures.
- [in] Specifies the information level of the data. This parameter can be one of the following values.
- bufptr
- [out] Pointer to the buffer that receives the data. The format of this data depends on the value of the
levelparameter. This buffer is allocated by the system and must be freed using theNetApiBufferFreefunction. Note that you must free the buffer even if the function fails withERROR_MORE_DATA.
- [out] Pointer to the buffer that receives the data. The format of this data depends on the value of the
- prefmaxlen
- [in] Specifies the preferred maximum length of returned data, in bytes. If you specify
MAX_PREFERRED_LENGTH, the function allocates the amount of memory required for the data. If you specify another value in this parameter, it can restrict the number of bytes that the function returns. If the buffer size is insufficient to hold all entries, the function returnsERROR_MORE_DATA.
- [in] Specifies the preferred maximum length of returned data, in bytes. If you specify
- entriesread
- [out] Pointer to a
DWORDvalue that receives the count of elements actually enumerated.
- [out] Pointer to a
- totalentries
- [out] Pointer to a
DWORDvalue that receives the total number of entries that could have been enumerated from the current resume position.
- [out] Pointer to a
- resumehandle
- [in/out] Pointer to a
DWORDvalue that contains a resume handle which is used to continue an existing search. The handle should be zero on the first call and left unchanged for subsequent calls. IfresumehandleisNULL, no resume handle is stored.
- [in/out] Pointer to a
Note that since the NetWkstaUserEnum function lists entries for service and batch logons, as well as for interactive logons, the function can return entries for users who have logged off a workstation. This can occur, for example, when a user calls a service that impersonates the user. In this instance, NetWkstaUserEnum returns an entry for the user until the service stops impersonating the user.
The following code sample demonstrates how to list information about all users currently logged on to a workstation using a call to the NetWkstaUserEnum function. The sample calls NetWkstaUserEnum, specifying information level 0 (WKSTA_USER_INFO_0). The sample loops through the entries and prints the names of the users logged on to a workstation
void CLoggedOnUsersPart2Dlg::OnButton1()
{
LPWKSTA_USER_INFO_0 pBuf = NULL;
LPWKSTA_USER_INFO_0 pTmpBuf;
DWORD dwLevel = 0;
DWORD dwPrefMaxLen = -1;
DWORD dwEntriesRead = 0;
DWORD dwTotalEntries = 0;
DWORD dwResumeHandle = 0;
DWORD i;
DWORD dwTotalCount = 0;
NET_API_STATUS nStatus;
wchar_t* pszServerName = NULL;
// The server is not the default local computer.
//
BOOL bRemote = ((CButton*)GetDlgItem(IDC_RADIO2))->GetCheck();
CString strServerName = "";
if (bRemote == TRUE)
{
((CEdit*)GetDlgItem(IDC_EDIT1))->GetWindowText(strServerName);
pszServerName = new wchar_t[strServerName.GetLength()+1];
if (pszServerName != NULL)
{
if (MultiByteToWideChar(CP_ACP, MB_PRECOMPOSED,
strServerName, -1, pszServerName, strServerName.GetLength()+1) == 0)
{// error
AfxMessageBox("Error when get wide char!", MB_ICONERROR | MB_OK);
delete pszServerName;
return;
}
}
}
//
// Call the NetWkstaUserEnum function, specifying level 0.
//
do // begin do
{
nStatus = NetWkstaUserEnum((char *)pszServerName,
dwLevel,
(LPBYTE*)&pBuf,
dwPrefMaxLen,
&dwEntriesRead,
&dwTotalEntries,
&dwResumeHandle);
//
// If the call succeeds,
//
if ((nStatus == NERR_Success) || (nStatus == ERROR_MORE_DATA))
{
if ((pTmpBuf = pBuf) != NULL)
{
m_lstUsers.DeleteAllItems();
//
// Loop through the entries.
//
for (i = 0; (i < dwEntriesRead); i++)
{
//assert(pTmpBuf != NULL);
if (pTmpBuf == NULL)
{
//
// Only members of the Administrators local group
// can successfully execute NetWkstaUserEnum
// locally and on a remote server.
//
AfxMessageBox("An access violation has occurred", MB_OK | MB_ICONERROR);
break;
}
//
// Print the user logged on to the workstation.
//
char strBuffer[256];
WideCharToMultiByte(CP_ACP, 0,
(unsigned short *)pTmpBuf->wkui0_username, -1, strBuffer, 256, NULL, NULL);
m_lstUsers.InsertItem(dwTotalCount, strBuffer);
pTmpBuf++;
dwTotalCount++;
}
}
}
//
// Otherwise, indicate a system error.
//
else
{
CString strError = "";
strError.Format("A system error has occurred: %d\n", nStatus);
AfxMessageBox(strError, MB_OK | MB_ICONERROR);
}
//
// Free the allocated memory.
//
if (pBuf != NULL)
{
NetApiBufferFree(pBuf);
pBuf = NULL;
}
}
//
// Continue to call NetWkstaUserEnum while
// there are more entries.
//
while (nStatus == ERROR_MORE_DATA); // end do
//
// Check again for allocated memory.
//
if (pBuf != NULL)
NetApiBufferFree(pBuf);
if (pszServerName != NULL)
{
delete pszServerName;
}
}
Note that we work with unicode string, so need to use WideCharToMultiByte() and MultiByteToWideChar().
Thanks Mila025, you helped me very much.
History
- 18th April, 2006: Initial post
