- home
- articles
- quick answersQ&A
-
discussionsforums
- CodeProject.AI Server
- All Message Boards...
- Application Lifecycle>
- Design and Architecture
- Artificial Intelligence
- ASP.NET
- JavaScript
- Internet of Things
- C / C++ / MFC>
- C#
- Free Tools
- Objective-C and Swift
- Database
- Hardware & Devices>
- Hosting and Servers
- Java
- Linux Programming
- Python
- .NET (Core and Framework)
- Android
- iOS
- Mobile
- WPF
- Visual Basic
- Web Development
- Site Bugs / Suggestions
- Spam and Abuse Watch
- featuresfeatures
- communitylounge
- help?
Everything / Security / Cryptography
Cryptography
cryptography
Great Reads
by Arpan Jati
RSA encryption library with full OAEP padding and private key encryption support
by Kewin Rausch
Design and development of a TOR-like protocol to keep your communication secure and your identity unknown
by Cryptonite
The Blum Micali algorithm provides for a cryptographically secure PRNG (pseudo random number generator).
Latest Articles
by Daniel Ramnath
C++,
by Daniel Ramnath
C++ OpenSSL 3.
by Michael Chourdakis
Use SHA-3 and the CRYSTALS Kyber,
by Sergey Alexandrovich Kryukov
Generator of highly secure passwords based on cryptographic hash and master password,
All Articles
15 Jul 2012 by
RSA encryption library with full OAEP padding and private key encryption support
15 Oct 2017 by Kewin Rausch
Design and development of a TOR-like protocol to keep your communication secure and your identity unknown
29 Jan 2018 by phil.o
5 Mar 2021 by Clark Fieseln
Low rate data exchange (e.g., chat) using audio steganography, ensuring privacy, anonymity and cybersecurity
14 Nov 2019 by CPallini
An assembly implementation of the AES-128 cipher algorithm for the 8051 microcontroller
7 Feb 2019 by Sibeesh Passion
Create own cryptocurrency and own private consortium network in Azure
8 May 2022 by Bruno Tabbia
Creation of a substitution box starting from a key and using it in a direct substitution cipher
30 Jun 2022 by raddevus
Fully working sample code and explanation of everything necessary to create authenticated encryption with AES256.
11 Oct 2013 by ASP.NET Community
At A large part of security in any web application is keeping your secrets secret. Cryptography makes that
9 Jan 2017 by Michael Haephrati
28 Dec 2022 by Sergey Alexandrovich Kryukov
Generator of highly secure passwords based on cryptographic hash and master password, which should be memorized; no password storage is involved.
26 Jul 2022 by raddevus
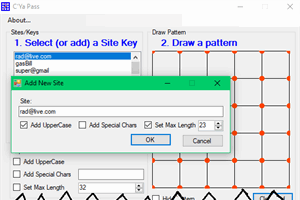
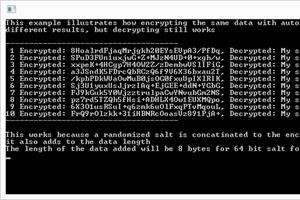
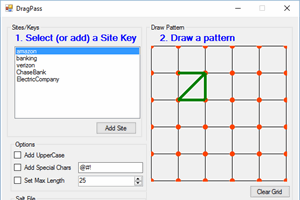
C’YaPass (Fully Open Source Software) now a Fully-Functioning Password Ecosystem which doesn’t store your passwords anywhere — You are the owner of your data.
22 Jul 2019 by Michael Chourdakis
20 Nov 2011 by Dominik Reichl
A C# implementation of the BLAKE hash algorithm.
6 Jun 2013 by Fernando E. Braz
6 Aug 2016 by raddevus
6 Oct 2014 by Pavel Durov
This article will explain briefly how to use a basic encryption/decryption on Android and on .NET platforms, with focus on passing encrypted data from Android to .NET.
30 Mar 2015 by Florian Rappl, Niki Kilbertus
Using Microsoft Azure to add advanced machine learning capabilities with connected IoT devices, which monitor activities of a baby and his or her environment.
5 May 2022 by Jerome Vonk
Description of cryptographic hashes and practical examples on how to calculate them
22 Sep 2022 by Raphael Amorim
25 Feb 2011 by Mario Majčica
16 Nov 2017 by raddevus
Complete source code that creates a solution so users never have to make up, memorize or type a password again
21 Apr 2011 by All Time Programming
Verifying the Server Certificate on the client side using a CA file
21 Mar 2016 by Dharmesh_Kemkar
21 Jan 2017 by Michael_Jacobsen
Encryption algorithm based on key self-mutation. Complete source code and samples.
13 Aug 2023 by Michael Chourdakis
26 Jan 2015 by 1337Architect
Handy classes to use the .NET Encryption/Decryption
3 Jun 2016 by raddevus
25 Apr 2011 by All Time Programming
23 May 2019 by Saira Fazal Qader
Conversion of image to byte and Encryption using 128 bit key than Decryption using the same key and re-conversion from byte to image
29 Jun 2016 by TimMackey
A simple demonstration of public key cryptography and a character substitution encryption method.